how to log a data breach
We know we must inform affected individuals without undue delay. Be sure to log into the affected accounts to change your password.

How To Deal With A Data Breach Of Your Personal Info Privacy Policies
Refer to the Office of the Australian Information Commission Respond to a data breach page for more steps you can take.

. All you need to do is put in your email address to get detailed information about your exposure to recent data breaches. These incidents can be intentional such as a database hack or accidental such as an employee emailing confidential files to the wrong recipient. Bad actors committing data breaches are often in search of information that can be used to steal money.
We know who is the relevant supervisory authority for our. Dealing with a data breach can be time-consuming and expensive. The middle ground and probably the easiest method to get you up and running is to send logs via the syslog protocol to a remote server.
It involves finding a breach shutting it down identifying what was stolen and notifying anyone who was affected. The breach can be intentional or accidental. Implement tools services and policies.
Tap Check Passwords and verify its you. GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded. If your password information is stolen your hacker will probably use it to log in elsewhere.
Discover the core of identity security. Review logs to determine who had access to the data at the time of the breach. The log should describe the incident itself the cause repercussions risk of future damage affected data and measures taken to mitigate the risks to further damage.
A personal data breach is. Confirm your account details which will go straight to the hacker. A data breach is when your personal data is accessed copied or changed by someone without your permission.
Credit and debit card numbers bank logins and private identifying information like. Data breaches involve theft or loss of private information such as. Include things like who needs to know what to do and when to release a data breach notification to the public.
Many data breaches will affect your passwords even if it also affects other data. Also analyze who currently has access determine whether that access is needed and restrict access if it is not. Most data breaches involve hacked email accounts and stolen bank information.
A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party. You should act on this type of breach as soon as possible. If your name and phone number were part of a data breach attackers can use it to try to log into your account.
Some online services allow you to view what devices have recently used your login details and any recent transactions. Review your account security settings. Verify the types of information compromised the number of people affected and whether you have contact information for those people.
Make it harder for hackers to log in to your accounts by creating two ways to gain access. This could include Social Security numbers credit card numbers bank account numbers health records and business information such as your list of clients. After thinking for a bit Google will display any issues its found including compromised reused and.
An email data breach can happen when there are security issues with an email. The first thing to do. Technically a data breach is a violation of security protocol for an organization or individual in which confidential information is copied transmitted viewed and stolen by an unauthorized person.
However sending it to a dedicated log management solution. This can be done on a white board or sheet of paper. The authority removed the report which it posted online on Tuesday as it failed to properly hide the names and personal details of those who.
This means creating a. Doing it right has moved beyond human capacity. We have a process to inform affected individuals about a breach when their rights and freedoms are at high risk.
A breach of security leading to the accidental or unlawful destruction loss alteration unauthorised disclosure of or access to personal data transmitted stored or otherwise processed in connection with the provision of a public electronic communications service. Click a link which could download malware to your device and allow them to hack your email. Data breacheswhether nefariously intentional or innocently accidentalopen people up to identity theft invasion of privacy and costly financial losses.
The second step is to map the constellation of situations and their stakeholders. If you get a breach email dont click any links or respond to the message as someone could be trying to scam you online. Change y our password s Keeping the same passwords for years makes you an easy target.
To make a secure. Ad Secure your enterprise. Meaning cybercriminals can gain access to your information through an organisation website or other places you have previously inputted your data.
To prepare for a data breach event policies actions and tools can be put in place to lay out a plan for detecting and containing an event while minimizing overall exposure in the first. A personal data breach may mean that someone. Responding to a personal data breach We have in place a process to assess the likely risk to individuals as a result of a breach.
You can usually also log out those devices from these settings. Dont worry if you already have. 1 day agoATHENS Greeces National Transparency Authority NTA was forced on Friday to remove a report on migrant pushbacks in the Aegean Sea as it was improperly redacted in an embarrassing data breach.
When you turn on multifactor. Enter the password for your Google account. Have a meeting to go over your contingency plan.
Data Breach Incident Log Template. Make sure the new password is secure and has nothing to do with the prior one. Sometimes a data breach involves financial information including credit card numbers or bank account information.
Create a document of your plan and store it somewhere your employees can.

Equifax Data Breach Why You Should Be Concerned And What To Do Data Breach Data Identify
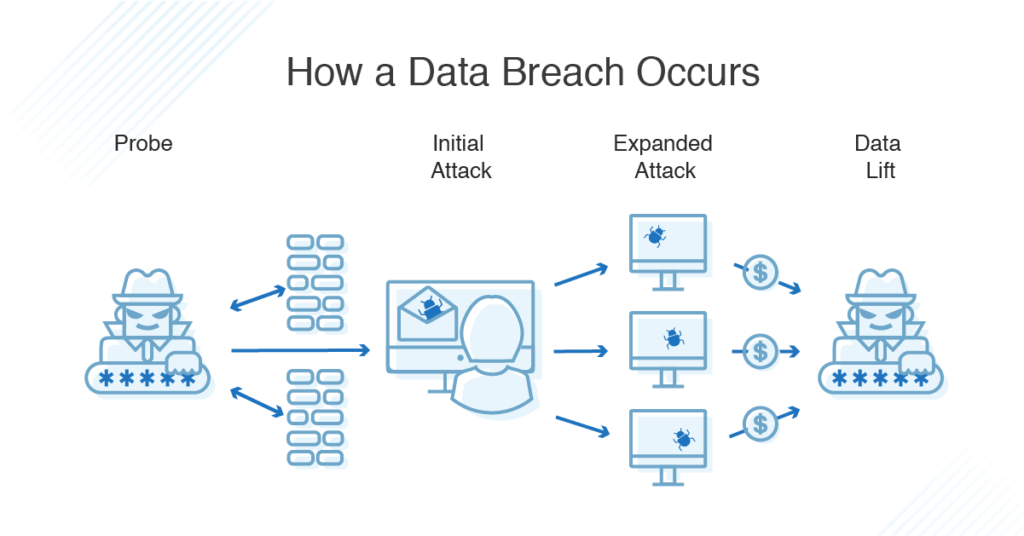
What Is A Data Breach Definition Types Dnsstuff

Common Data Breach Causes Cyber Security Awareness Infographic Marketing Data Breach
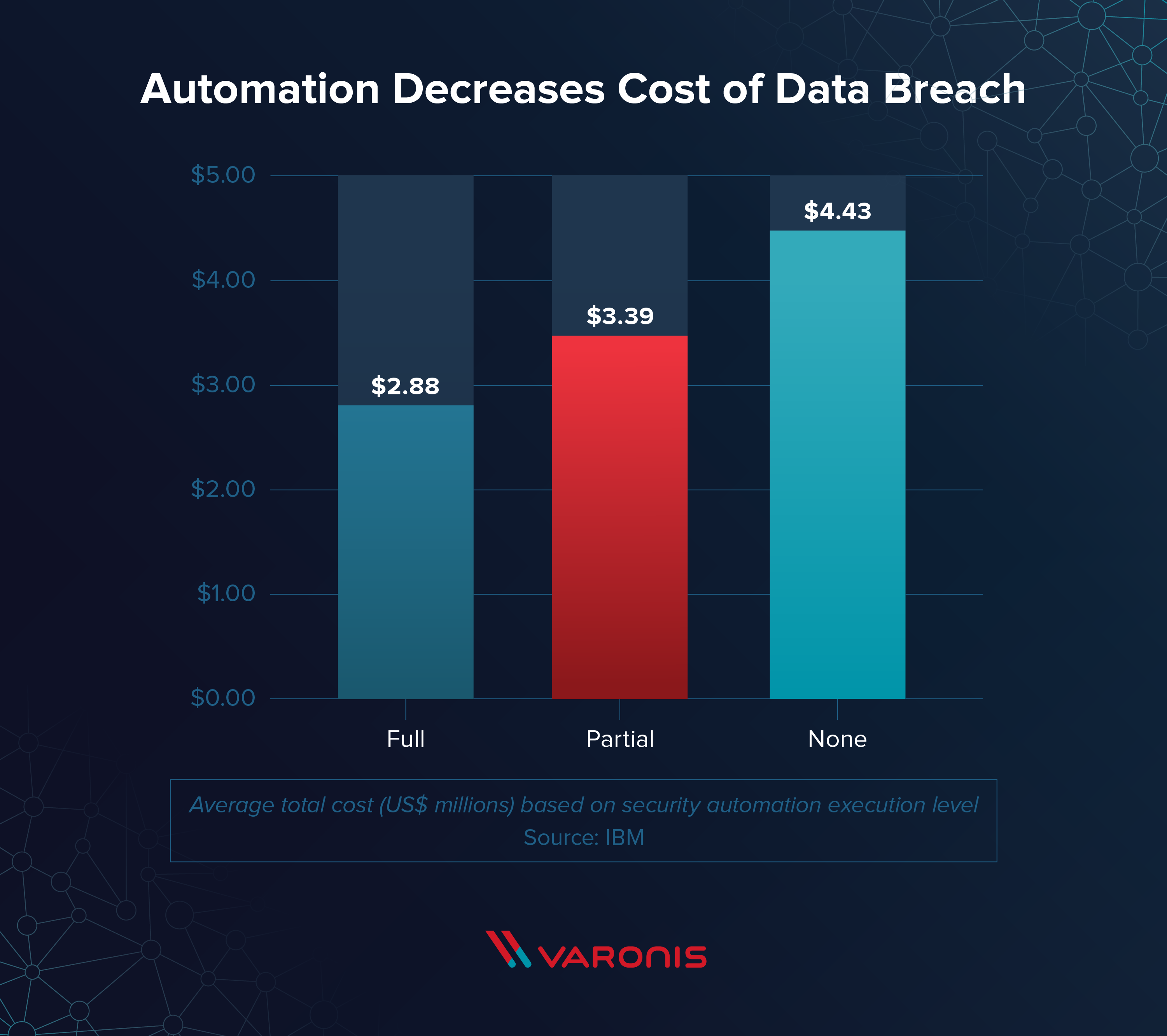
Data Breach Response Times Trends And Tips

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
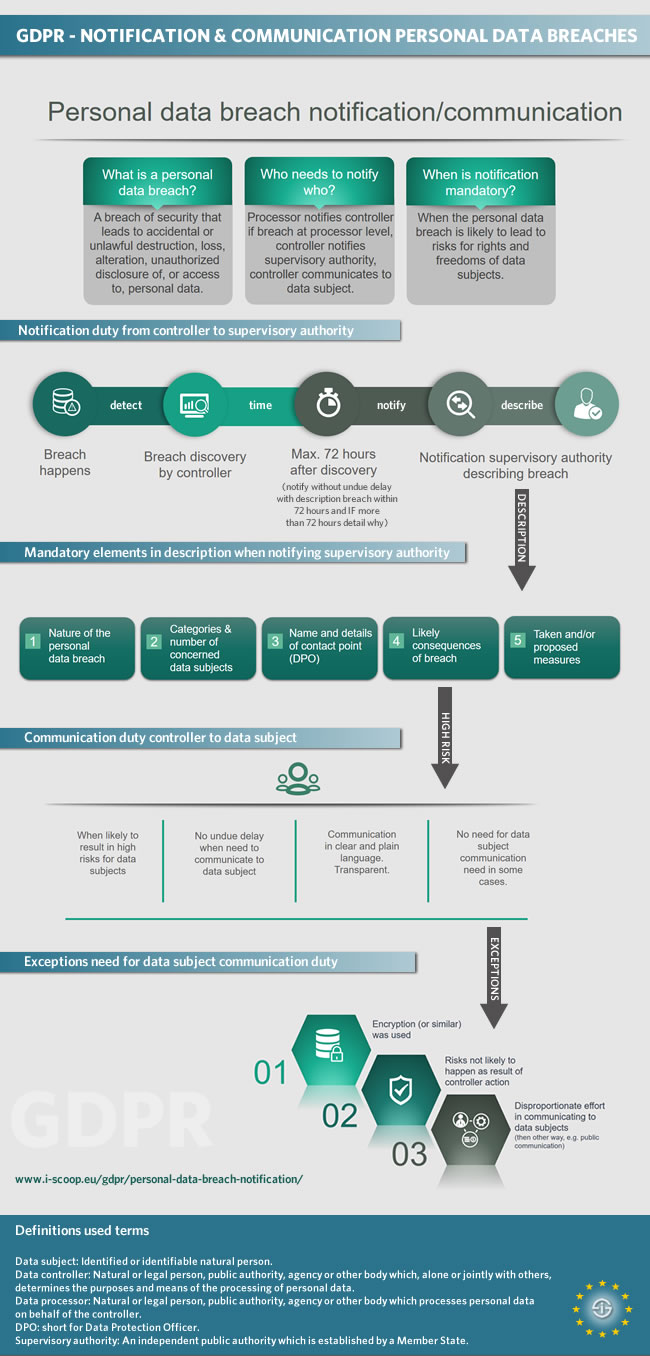
Personal Data Breach Notification And Communication Under Gdpr
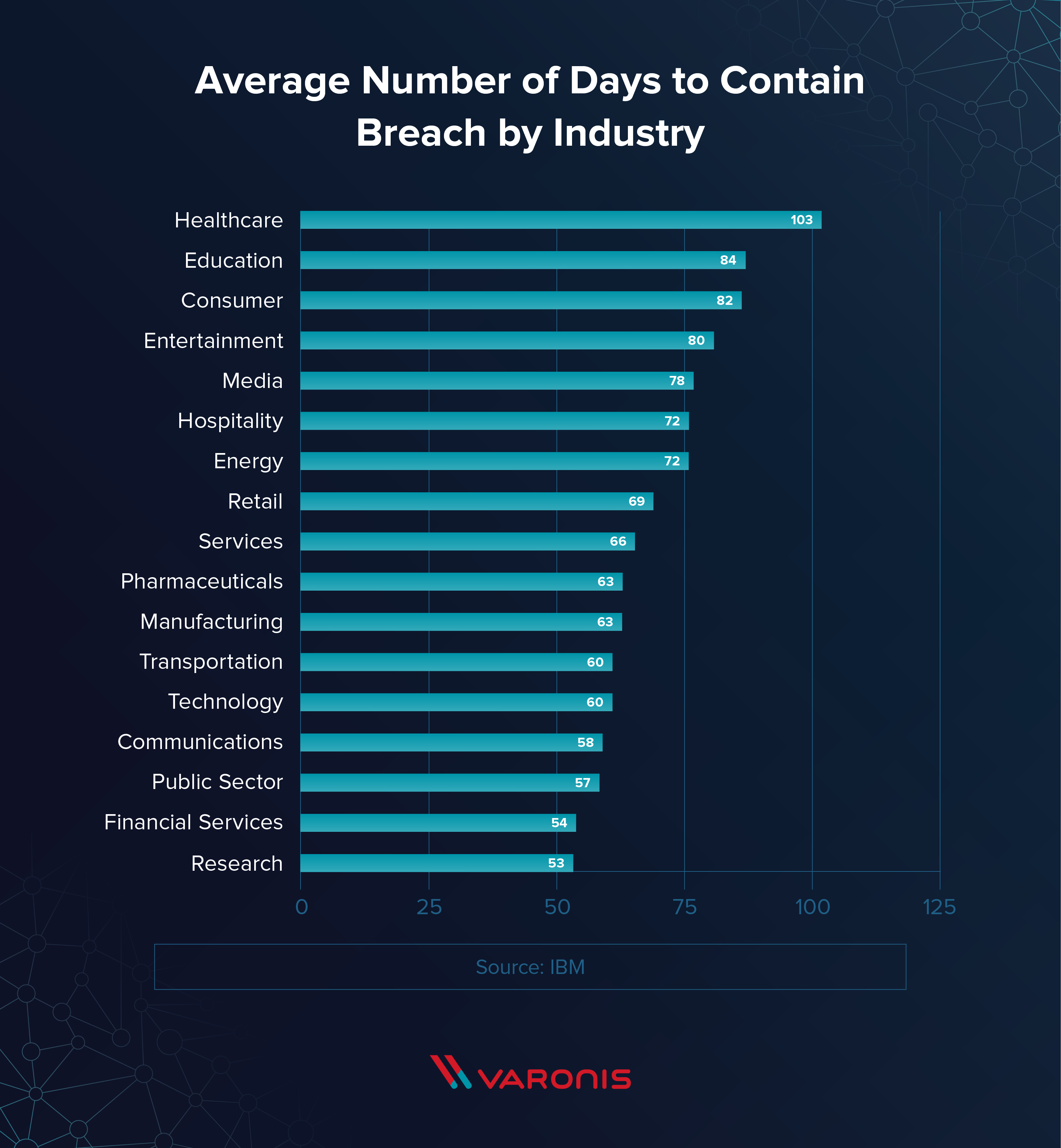
Data Breach Response Times Trends And Tips

Data Breach Infographic Data Breach Shocking Facts Infographic

Gdpr 4 Passi Verso La Conformita 2 4 Key4biz Lezioni Di Informatica Sicurezza Informatica Conformismo

Data Breach Response Times Trends And Tips

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Onelogin Businesses Vulnerable To Data Breaches By Ex Employees Data Breach Data Vulnerability

Data Breach Statistics 2011 Security Computer Security Data Breach

Respect And Protect Your Customers Data Data Data Breach Respect

13 Critical Data Breach Stats For Australian Businesses In 2022 Upguard

Impact Of Data Breach On The Legal Industry Infographic Data Breach Productivity Infographic Educational Infographic

How To Write Gdpr Compliant Data Breach Notification Letters Privacy Policies
